Kleopatra Pgp Download
Status: in progress
Kleopatra allows for the management of all certificates (OpenPGP and S/MIME) in one tool. Certificate Server Kleopatra provides a simple import and export of certificates from and to (OpenPGP and X.509) certificate servers (also called key servers).
Contents
In case of Gpg4win you can also search for key on the key server via Kleopatra. PGP Desktop also has such function. After making sure that the downloaded key match with the key downloaded from the key server, you can import it to your key store. Pinentry-curses does not work for Kleopatra. Kleopatra may work with gnupg 1, too but the selftest will warn about this and some functionality will be unavailable. It should depend on gnupg2. GnuPG 2.1.x is supported, too. You can use Kleopatra's selftest to check your packaging it should show no errors. Kleopatra is a certificate manager which you can use to manage your keys, but today we will be using Enigmail instead. Installing Thunderbird. The first step is to make your way to the Thunderbird website, then hit the big green Download button in the middle. Keeping this in consideration, where can I download Kleopatra? Select Download Gpg4win Go to your Downloads folder and run the gpg4win- file. Select all of the default options of the installer to install Gpg4win. Navigate to C:Program FilesGNUGnuPG and run the Kleopatra application. Just download the zip-File and unzip it onto your usb-pendrive. Then simply change into the folder gpg4usb at your usb-drive, and execute the binary in there: startlinux or startwindows.exe - should be easy to determine, which one's yours;) Have a lot of fun! We will learn how to use PGP encryption to send encrypted messages to anyone. How to do the setup. Download software from here; Click on the exe file, install it with all default settings; Generate the keypair; Once installation is complete, below screen will come. Click on New Key Pair — you can provide any random values.
- Kleopatra Test Plan
- Tests
Introduction
The purpose of this test plan is to ensure Kleopatra works well on all supported operating systems.
Test environment
Terminal server license key. Choose one combination of the following target platforms supported by Kleopatra.
Operating system:
- Windows Vista (32 or 64bit)
- Windows 7 (32 or 64bit)
- Windows 8 (32 or 64bit)
- Windows 10 (32 or 64bit)
It is recommended to use a clean virtual test environment, e.g. with VirtualBox.
Preconditions
- GnuPG (latest release) installed
- Kleoptra installed
- OpenPGP public key (*.asc or *.gpg) and private key (*.asc or *.gpg)
- S/MIME certificate chain (*.pem) and private key (*.p12)
Tests
Testsuite 1: OpenPGP
1.1: Create certificate
- Choose 'File' from menu bar
- Click 'New Keypair'
- Choose 'OpenPGP Keypair'
- Fill in some random information
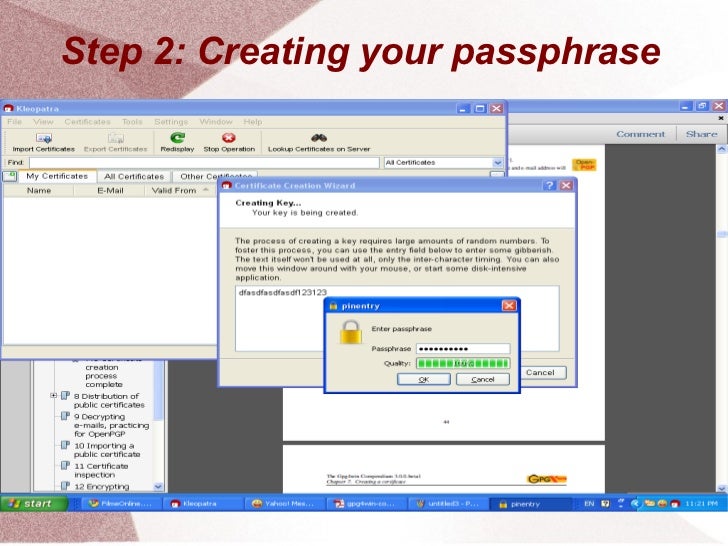
- Choose a passphrase
- The new certificate will appear in the overview
1.2: Import certificates
- Click the 'Import' button
- Navigate to a previously exported certificate
- Click 'Open'
- The imported certificate will appear in the overview
1.3: Encrypt file
- Click the 'Sign/Encrypt Files' button
- Choose a file
- Deselect the 'Sign' option
- Select an OpenPGP certificate as target
- Click the 'Sign/Encrypt' button
- An encrypted file is at the defined target
1.4: Sign file
- Click the 'Sign/Encrypt' button
- Choose a file
- Deselect the 'Encrypt' option
- Select an OpenPGP certificate as signing source
- Click the 'Sign/Encrypt' button
- A signed file is at the defined target
1.5: Sign & encrypt file
- Click the 'Sign/Encrypt' button
- Choose a file
- Select an OpenPGP certificate as signing source
- Click the Sign/Encrypt button
- A signed and encrypted file is at the defined target
1.6: Decrypt file
- Click the 'Verify/Decrypt' button
- Choose an OpenPGP encrpyted file
- Enter the passphrase
- A decrypted file is at the defined target
1.7: Verify file
- Click the 'Verify/Decrypt' button
- Choose an OpenPGP signature file
- A result dialog shows the signature details
1.8: Create certificate server
- Select 'Settings' in menu bar
- Click the 'Configure Kleopatra.'
- Click on 'New' and select 'OpenPGP' in the certificate server dialogue
- Confirm the server details
1.9: Lookup key on server
- Click on 'Lookup on Server'
- Search for a name (i.E. 'Einstein')
- Select a key
- Click the 'Import' button
- The imported key appears in the 'Imported Certificates' tab
1.10: Export public and private key
- Right click on an OpenPGP key
- Click 'Export.'
- Select a location in the dialogue
- Click the 'Save' button
- The exported public key is at the choosen location
1.11: Export secret key
- Right click on a key you created before
- Click 'Export Secret Keys.'
- Select a location and enter a filename in the dialogue
- Click 'Ok'
- Enter passphrase
- The exported secret key is at the choosen location
1.12: Certify a certificate
- Select a previously imported public key
- Click 'Certify' button
- Select the UIDs you want to certify
- Approve, that fingerprints are checked
- Step 2: Select your certificate and keep option 'Certify only for myself'
- Click 'Certify' button
- Enter the passphrase of your identity
- Finish the dialogue
- Open the certificate details of the previously certified key (via double click)
- The Trust Level column shows now 'full'
1.13: Change owner trust
- Right click on an imported public key
- Select 'Change Owner Trust.'
- Select one of the given options and confirm with 'OK'.
1.14: Sign & encrypt folder
- Click on 'File' in the menu bar
- Select 'Sign/Encrypt Folder.'
- Select a folder
- Click the 'Sign/Encrypt' button
- Enter your passphrase
- The encrypted folder is at the selected destination (as tar.gpg archive)
1.15: Create revocation certificate
- Open certificate details of your own OpenPGP certificate
- Click 'Generate revocation certificate' button
- Select location and enter filename
- Enter passphrase
- The revocation certificate is at the selected destination
1.16: Import revocation certificates
- Open previously created revocation certificate file in editor and remove manually the comment (until '-----BEGIN PGP PUBLIC KEY BLOCK-----').
- Click on 'Import' button
- Select the revocation certificate
- Click 'Import'
- Open the certificate details of the previously certified key (via double click)
- The Trust Level column shows now 'revoked'
1.17: Check trust chains in Web of Trust
- Create two additional OpenPGP certificates
- Set the owner trust with your first certificate on the second certificate
- Change the trust with the second certificate on the third
- Sign with the second certificate on the third
- Export the public key of the second and third key
- Delete the second and third key
- Import the public keys of the second and third key
- Check the trust on the third key
1.18: Change validity
- Open certificate details of your own OpenPGP certificate
- Click on 'Change' next to the 'Expires' option
- Select a date
- Click 'OK'
1.19: Check subkeys
- Open certificate details of an OpenPGP certificate
- Choose 'More Details'
- Check the existing subkeys
1.20: Add new UID to key
- Open certificate details of your own OpenPGP certificate
- Click 'Add email address'
- Enter some random information
- Click 'OK'
- Enter your passphrase
- The new UID is listed in the certificate details table
1.21: Create new OpenPGP certificate using ECC Brainpool
- Choose 'File' from menu bar
- Click 'New Keypair'
- Choose 'OpenPGP Keypair'
- Enter some random information
- Click 'Advanced Options.'
- Select the 'ECDSA' option
- Choose a 'brainpool' alogrithm
- Click 'OK'
- Click 'Next' in the initial dialogue
- Enter a passphrase
- The created key appears in the overview
1.22: Check integrity of downloaded files with signatures
- Download a file and the signature of it (e.g. https://www.gnupg.org/download/)
- Download the signing keys (e.g. https://www.gnupg.org/signature_key.html)
- Import the signing keys
- Click the 'Decrypt/Verify' button in toolbar
- Select the downloaded signature file
- A result dialog shows the signature details
1.23: Decrypt file that was encrypted under GNU/Linux
- Click the 'Decrypt/Verify' button in toolbar
- Select the encrypted file
- Enter your passphrase
- A decrypted file is at the defined target
1.24: Check signature on file that was signed under GNU/Linux
- Click the 'Decrypt/Verify' button in toolbar
- Select the signature file
- A result dialog shows the signature details
1.25: Export key with Paperkey
- Right click on private key
- Select 'Print Secret Key.' Option
- Save or print the resulting file
1.26: Import key with Paperkey
- Delete Private Key
- Right click on public key
- select further details
- right click private key and select the import printed key option
- select txt file with exported key
1.27: Check trust levels (with new model)
Testsuite 2: X.509
2.1: Create Certificate-Request
- Choose 'File' from menu-bar
- Click 'New Secret Key'
- Choose 'X.509 Keypair'
- Fill some random information
- Choose a passphrase
- Save the certificate request to file
2.2: Import Certificates incl. Trustchain
- Choose 'File' from menu-bar
- Click 'Import.'
- Navigate to a previously exported certificate
- Click 'Open'
- The imported certificate will appear in the overview
2.3: Encrypt Files
- Click the 'Sign/Encrypt Files' button
- Choose a file within the dialogue
- Deselect the 'Sign' option
- Select an X.509 certificate as target
- Click the 'Sign/Encrypt' button
- An encrypted file is at the defined Target
2.4: Sign Files
- Click the 'Sign/Encrypt Files' button
- Choose a file within the dialogue
- Deselect the 'Encrypt' option
- Select an X.509 certificate as signing source
- Click the 'Sign/Encrypt' button
- An signed file is at the defined Target
2.5: Sign & Encrypt Files
- Click the 'Sign/Encrypt Files' button
- Choose a file within the dialogue
- Select an X.509 certificate as signing source
- Click the 'Sign/Encrypt' button
- An signed and enncrypted file is at the defined target
2.6: Decrypt Files
- Click the 'Verify/Decrypt Files' button
- Choose a file encrpyted to a X.509 certificate within the dialogue
- Enter the passphrase
- A decrypted file is at the defined target
2.7: Lookup Key on Server
If no Server is defined, please execute Testsuite 2.10 first.
- Click on 'Lookup on Server'
- Search for a name (i.E. 'Einstein')
- Select a key
- Click the 'Import' button
- The imported key appears in the 'Imported Certificates' tab
2.8: Certificate Revocation List
- Select 'Extras' in the menu-bar
- Choose the 'Import Revocation List from File' option
- Select the revocation certificate list on the file dialogue
Kleopatra Pgp Download Mac
2.9: Check Mixed Encryption with X.509 and OpenPGP
- Select the 'File Sing/Encrypt' option
- Select a file from the file dialogue
- Deselect the 'Sign' option
- Select two recipients, one OpenPGP and X.509 certificate
- Click the 'Sign/Encrypt' button
2.10: Create Certificate Server
- Select 'Settings' in menu-bar
- Click the 'Kleopatra Settings'
- Click on 'New' and select X.509 in the certificate server dialogue
- Enter the details of your server
2.11: Export Trustchain
- Right click on your own X.509 root
- Choose 'Export Certificates'
- Select a destination to save to
- Click 'Save'
2.12: Check Certificate Details
- Right click a certificate
- Choose 'Details'
- Choose 'More Details'
- Check the certificate dump
2.13: Decrypt File that was encrypted under GNU/Linux
- Select the 'Check and Decrypt Files' option
- Select the encrypted file
- Enter your passphrase
2.14: Check Signature on File that was signed under GNU/Linux
- Select the 'Check and Decrypt Files' option
- Select the signed file
Testsuite 3: Smartcard OpenPGP (v2.1)
3.1: Initialize OpenPGP Smartcard
- Shutdown Kleopatra
- Put the smartcard into your reader
- Start Kleopatra
- Choose 'Tools' from the menu-bar
- Select 'Smartcard'
- Press 'F5' if no information is shown
- Click 'Generate New Keys' in the window
- Enter some random information
- Click 'Generate Keys'
3.2: Use OpenPGP Smartcard for Encryption
3.3: Use OpenPGP Smartcard for Signing
Testsuite 4: Smartcard X.509 (NetKey)
4.1: Use X.509 Smartcard for Encryption
4.2: Use X.509 Smartcard for Signing
4.3: Use X.509 Smartcard for Trusted Signing
We have been using Network Associates PGP 6.5.8 for 10+ years (mainly to just decrypt files that we get from our customers). We recently had a customer that everything was working just fine until a new person took over the position that sends us files. It was reported to me that they use GPG4WIN / Kleopatra but I could not get them to tell me version. I started testing by downloading the latest (3.1.4) and was able to duplicate the problem - when I encrypt a file on GPG4WIN / Kleopatra and then attempt to decrypt on Network Associates PGP 6.5.8 I get the following error: An error has occurred - encrypted session key is bad.
Pgp Encryption Kleopatra
I read online to set the following:
Click on Settings -> Configure Kleopatra (screen pics below)
OpenPGP -> “compliance” set to pgp6
S/MIME -> Use Cipher Algorithm set to 3DES
Still had no success, so I figured since they were positive it worked in the past I would download an older version (3.0.1). As soon and it was installed, I encrypted a file and then I was able to decrypt it just fine using Network Associates PGP 6.5.8
I was able to verify the setting above were still set.
avg cleaner activation code free I was asked to 'upgrade' the 3.0.1 to 3.1.4 (by Admin) and once installed it still fails (meaning I can encrypt but the decrypt on Network Associates PGP 6.5.8 still gives the same error (An error has occurred - encrypted session key is bad).
I am not sure if this is a bug or if there is a setting I am missing.
Download Kleopatra Desktop App
I also know there are 5-6 version between 3.0.1 and 3.1.4, so I am not sure where it started having the problem.
/suprema-fingerprint-scanner-driver-download.html. Any help would be greatly appreciated.